Zeotap has just achieved its SOC 2 Type 1 compliance certification – here, we unpack what this means and why it’s an important credential to look for when evaluating cloud-based technologies.
What is SOC 2 compliance?
SOC 2 is awarded by the American Institute of Certified Public Accountants (AICPA) to certify that a service organisation that stores customer data in the cloud is following the right practices and controls to safeguard the privacy and security of that data.
In a nutshell, a service provider with SOC 2 compliance has proven that it:
- is consistently monitoring for any potentially threatening activity
- is set up to recognise and handle threats to protect data
- has processes in place to resolve any security incidents and restore data
As a Customer Data Platform, Zeotap has committed to SOC 2 compliance in order to assure our clients that their customer data is safe and secure, saving them (and their Data Protection Officers) the time and expense of conducting their own audits of our practices.
Who needs to have SOC 2 compliance?
Essentially, any service providers storing customer data in the cloud should look to achieve SOC 2 compliance. This covers many SaaS and PaaS companies, and the partners that they work with.
Is SOC 2 compliance important?
In a word, yes. Of course, SOC 2 is one of many privacy and security seals that service providers need if they’re handling customer data – others include ISO/IEC 27001 and CSA Star – but it’s a particularly critical one.
Firstly, because it’s one of the few ways that a potential customer can tell if a service provider is fully up-to-speed on GDPR. One of the inherent challenges with GDPR is that compliance is treated very much as an exercise of negative reinforcement – in other words, punishing those who are not compliant (and there have been many examples of this lately). What’s absent is a positive reinforcement i.e. enabling organisations to validate and show that they are compliant.
SOC 2 compliance – despite being awarded by a body based in the US – has grown in popularity among service providers because it fills that gap. Obtaining certification here is an excellent means of showing that an organisation is continuously taking the right steps to deliver GDPR compliance.
Secondly, because it asks a service provider to ‘walk the walk’ as much as ‘talk the talk’. More on exactly what that means next…
What does it take to achieve SOC 2 compliance?
SOC 2 compliance audits set out to test whether a service provider is in compliance with the AICPA’s Trust Services Criteria (TSA), which can be seen in full detail here. The audit is performed by an independent CPA (Certified Public Accountant) or accountancy organisation, who follow strict guidance on audit procedures and are regularly reviewed.
The ‘walking the walk’ refers to the fact that the process of auditing is extended (often six-twelve months) because the auditor is reviewing not just a set of ‘on-paper’ processes, but looking for continuous evidence of whether these processes are being properly executed. It’s for this reason that SOC 2 is such an important credential to look for in a cloud-based provider, as it shows that data security and privacy best practices are operationally integral to how they work.
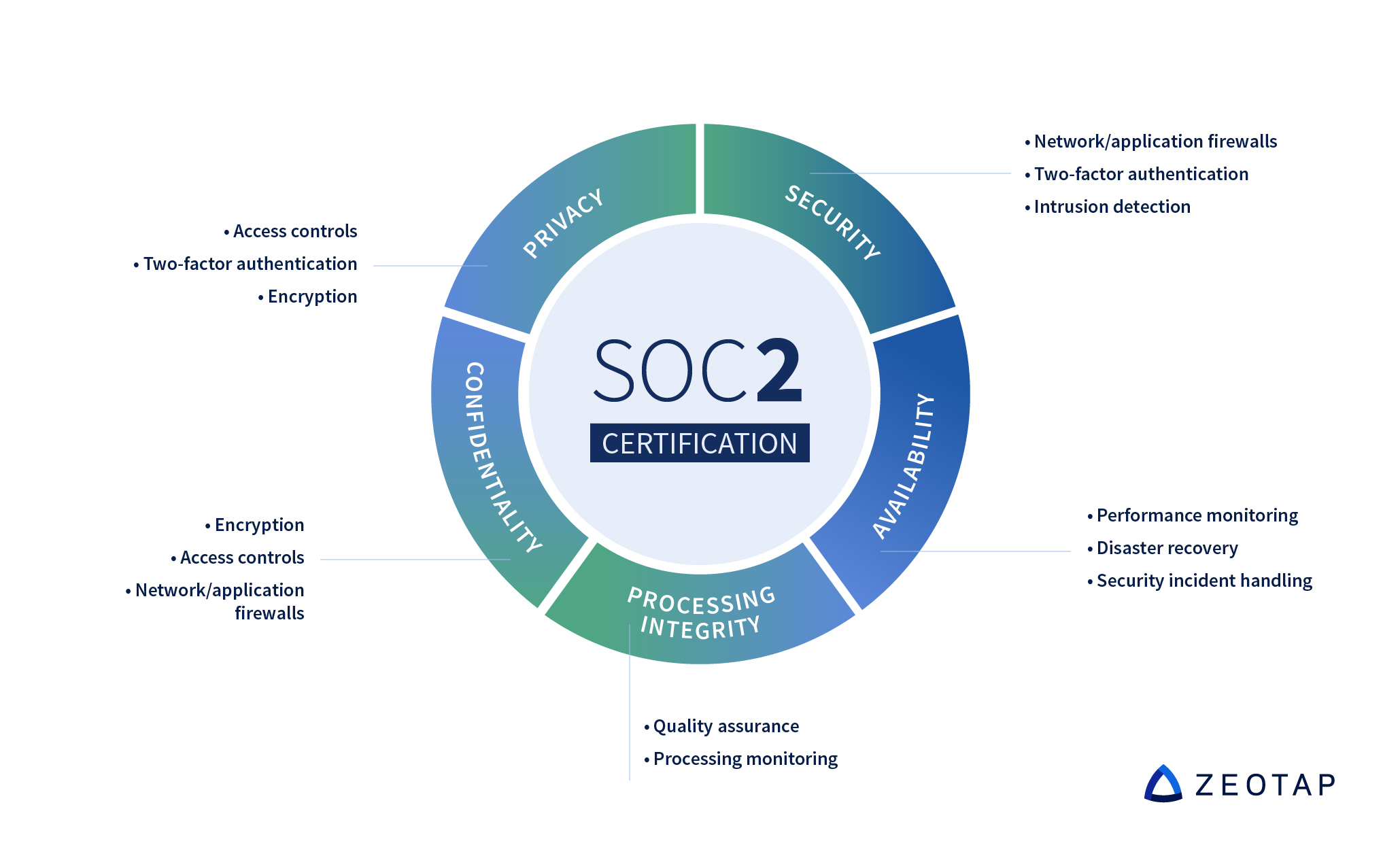
The process audits based on the five principles below:
Availability
The system is available per the agreement between user and provider. The service provider also needs to fully document business continuity and disaster recovery plans and procedures, and the auditor needs to be satisfied with the reliability and quality of the network.
Security
To comply with the Security principle, an auditor will verify that the system is adequately protected against outside access. This involves checks on both physical and digital access measures, including password parameters, firewalls and encryption.
Confidentiality
This principle relates to data that is designated ‘confidential’ – for example, a customer’s financial data submitted for use only by company employees. Similar to the Security principle, the auditor will check measures such as encryption and access controls.
Processing integrity
When looking at processing integrity, the auditor reviews whether the platform processes data in a way that is complete and accurate, and that any errors are accounted for.
Privacy
Last but not least, the Privacy principle of SOC 2 compliance concerns itself with Personal Identifiable Information (PII), such as names, phone numbers and email addresses. Amongst other things, data subjects must have the ability to opt-in and opt-out, as well as have the ability to request all their data be provided and deleted when they opt-out.
In conclusion
In today’s fast-evolving cloud software environment, it’s critical that any new vendors you bring on board are executing best practices when it comes to privacy and security. SOC 2 compliance, though far from the only measure of such things, is a critical ‘must have’ for any potential partner handling your customers’ data.